HiddenLayer, a Gartner recognized Cool Vendor for AI Security, is the leading provider of Security for AI. Its security platform helps enterprises safeguard the machine learning models behind their most important products. HiddenLayer is the only company to offer turnkey security for AI that does not add unnecessary complexity to models and does not require access to raw data and algorithms. Founded by a team with deep roots in security and ML, HiddenLayer aims to protect enterprise’s AI from inference, bypass, extraction attacks, and model theft. The company is backed by a group of strategic investors, including M12, Microsoft’s Venture Fund, Moore Strategic Ventures, Booz Allen Ventures, IBM Ventures, and Capital One Ventures.
Sep 12, 2024
Eval on query parameters allows arbitrary code execution in Weaviate integration
CVE Number
CVE-2024-45846
Summary
An arbitrary code execution vulnerability exists inside the select function of the mindsdb/integrations/handlers/weaviate_handler/weaviate_handler.py file in the Weaviate integration. The vulnerability requires the attacker to be authorized on the MindsDB instance and allows them to run arbitrary Python code on the machine the instance is running on. The vulnerability exists because of the use of an unprotected eval function.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.3.0 up to v24.7.4.1.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’)
Details
To exploit this, an attacker must be authenticated to a MindsDB instance that has the Weaviate integration installed. The vulnerability can be exploited if an embedding vector filter is present because the argument for the embeddings column in a ‘SELECT WHERE’ clause is passed to an eval statement in the select function of the mindsdb/integrations/handlers/weaviate_handler/weaviate_handler.py file (shown below – edited to only include the relevant sections).
def select(
self,
table_name: str,
columns: List[str] = None,
conditions: List[FilterCondition] = None,
offset: int = None,
limit: int = None,
) -> HandlerResponse:
...
# check if embedding vector filter is present
vector_filter = (
None
if not conditions
else [
condition
for condition in conditions
if condition.column == TableField.SEARCH_VECTOR.value
or condition.column == TableField.EMBEDDINGS.value
]
)
...
if vector_filter:
# similarity search
# assuming the similarity search is on content
# assuming there would be only one vector based search per query
vector_filter = vector_filter[0]
near_vector = {
"vector": eval(vector_filter.value)
if isinstance(vector_filter.value, str)
else vector_filter.value
}
query = query.with_near_vector(near_vector)The eval function appears to be used for parsing valid Python data types from arbitrary user input but has the side effect of enabling arbitrary code execution because Python code can be passed to it via the method explained above.
Eval on query parameters allows arbitrary code execution in Vector Database integrations
CVE Number
CVE-2024-45847
Summary
An arbitrary code execution vulnerability exists inside the _dispatch_update function of the mindsdb/integrations/libs/vectordatabase_handler.py file. The vulnerability requires the attacker to be authorized on the MindsDB instance and allows them to run arbitrary Python code on the machine the instance is running on. The vulnerability exists because of the use of an unprotected eval function, which can be used with multiple integrations.
Products Impacted
This vulnerability is present in MindsDB versions v23.11.4.2 up to v24.7.4.1.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’)
Details
To exploit this, an attacker must be authenticated to a MindsDB instance that has any of these affected integrations installed:
- PgVector
- Milvus
- LanceDB
- Xata
- Qdrant
- Pinecone
- ChromaDB
- WeaviateDB
The vulnerability exists because the argument for the embeddings column in an ‘UPDATE’ statement is passed into an eval statement in the _dispatch_update function of the mindsdb/integrations/libs/vectordatabase_handler.py file (shown below – edited to only include the relevant sections).
This function is part of the VectorStoreHandler class, which all of the vulnerable integrations inherit from. The eval function appears to be used for parsing valid Python data types from arbitrary user input, but has the side effect of enabling arbitrary code execution because Python code can be passed to it via the method explained above.
Eval on query parameters allows arbitrary code execution in ChromaDB integration
CVE Number
CVE-2024-45848
Summary
An arbitrary code execution vulnerability exists inside the insert function of the mindsdb/integrations/handlers/chromadb_handler/chromadb_handler.py file in the ChromaDB integration. The vulnerability requires the attacker to be authorized on the MindsDB instance, and allows them to run arbitrary Python code on the machine the instance is running on. The vulnerability exists because of the use of an unprotected eval function.
Products Impacted
This vulnerability is present in MindsDB versions v23.12.4.0 up to v24.7.4.1.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’)
Details
To exploit this, an attacker must be authenticated to a MindsDB instance that has the ChromaDB integration installed. The vulnerability exists because the value provided for the metadata column in an ‘INSERT’ statement is passed into an eval statement in the insert function in the mindsdb/integrations/handlers/chromadb_handler/chromadb_handler.py file (shown below – edited to only include the relevant sections).
def insert(self, table_name: str, data: pd.DataFrame):
"""
Insert data into the ChromaDB database.
"""
collection = self._client.get_or_create_collection(name=table_name)
# drop columns with all None values
data.dropna(axis=1, inplace=True)
# ensure metadata is a dict, convert to dict if it is a string
if data.get(TableField.METADATA.value) is not None:
data[TableField.METADATA.value] = data[TableField.METADATA.value].apply(
lambda x: x if isinstance(x, dict) else eval(x)
)
...The eval function appears to be used for parsing valid Python data types from arbitrary user input but has the side effect of enabling arbitrary code execution because Python code can be passed to it via the method explained above.
Eval on query parameters allows arbitrary code execution in SharePoint integration list creation
CVE Number
CVE-2024-45849
Summary
An arbitrary code execution vulnerability exists inside the create_a_list function of the mindsdb/integrations/handlers/sharepoint_handler/sharepoint_api.py file in the Microsoft SharePoint integration. The vulnerability requires the attacker to be authorized on the MindsDB instance and allows them to run arbitrary Python code on the machine the instance is running on. The vulnerability exists because of the use of an unprotected eval function.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.5.0 up to v24.7.4.1.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’)
Details
To exploit this, an attacker must be authenticated to a MindsDB instance that has the SharePoint integration installed. The vulnerability exists because the value provided for the list column in an ‘INSERT’ statement for the lists table is passed into an eval statement within the create_a_list function in the mindsdb/integrations/handlers/sharepoint_handler/sharepoint_api.py file (shown below – edited to only include the relevant sections).
def create_a_list(
self, site_id: str, list_template: str, display_name: str, column: str = None
) -> None:
"""
Creates a list with metadata information provided in the params
site_id: GUID of the site where the list is to be created
list_template: a string which contains the list template information (type of list)
eg.- "{'template': 'documentLibrary'}"
display_name: the display name of the given list, which will be displayed in the site
column: specifies the list of columns that should be created for the list
eg.- "[{'name': 'Author', 'text': { }},{'name': 'PageCount', 'number': { }}]"
Returns
None
"""
url = f"https://graph.microsoft.com/v1.0/sites/{site_id}/lists/"
payload = {}
if column:
column = eval(column)
payload["column"] = column
...The eval function appears to be used for parsing valid Python data types from arbitrary user input but has the side effect of enabling arbitrary code execution because Python code can be passed to it via the method explained above.
Eval on query parameters allows arbitrary code execution in SharePoint integration site column creation
CVE Number
CVE-2024-45850
Summary
An arbitrary code execution vulnerability exists inside the create_a_site_column function of the mindsdb/integrations/handlers/sharepoint_handler/sharepoint_api.py file in the Microsoft SharePoint integration. The vulnerability requires the attacker to be authorized on the MindsDB instance and allows them to run arbitrary Python code on the machine the instance is running on. The vulnerability exists because of the use of an unprotected eval function.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.5.0 up to v24.7.4.1.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’)
Details
To exploit this, an attacker must be authenticated to a MindsDB instance that has the SharePoint integration installed. The vulnerability exists because the value provided for the text column in an ‘INSERT’ statement for the siteColumns table is passed into an eval statement in the create_a_site_column function in the mindsdb/integrations/handlers/sharepoint_handler/sharepoint_api.py file (shown below – edited to only include the relevant sections).
def create_a_site_column(
self,
site_id: str,
enforce_unique_values: bool,
hidden: bool,
indexed: bool,
name: str,
text: str = None,
) -> None:
"""
Creates a list with metadata information provided in the params
site_id: GUID of the site where the column is to be created
enforced_unique_values: if true, no two list items may have the same value for this column
hidden: specifies whether the column is displayed in the user interface
name: the API-facing name of the column as it appears in the fields on a listItem.
text: details regarding the text values in the column
Returns
None
"""
url = f"https://graph.microsoft.com/v1.0/sites/{site_id}/columns/"
payload = {}
if text:
text = eval(text)
payload["text"] = text
...The eval function appears to be used for parsing valid Python data types from arbitrary user input but has the side effect of enabling arbitrary code execution because Python code can be passed to it via the method explained above.
Eval on query parameters allows arbitrary code execution in SharePoint integration list item creation
CVE Number
CVE-2024-45851
Summary
An arbitrary code execution vulnerability exists inside the create_an_item function of the mindsdb/integrations/handlers/sharepoint_handler/sharepoint_api.py file in the Microsoft SharePoint integration. The vulnerability requires the attacker to be authorized on the MindsDB instance and allows them to run arbitrary Python code on the machine the instance is running on. The vulnerability exists because of the use of an unprotected eval function.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.5.0 up to v24.7.4.1.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-95: Improper Neutralization of Directives in Dynamically Evaluated Code (‘Eval Injection’)
Details
To exploit this, an attacker must be authenticated to a MindsDB instance that has the SharePoint integration installed. The vulnerability exists because the value provided for the fields column in an ‘INSERT’ statement for the listItems table is passed into an eval statement in the create_an_item function in the mindsdb/integrations/handlers/sharepoint_handler/sharepoint_api.py file.
def create_an_item(self, site_id: str, list_id: str, fields: str) -> None:
"""
Creates an item with metadata information provided in the params
site_id: GUID of the site where the list id present
list_id: GUID of the list where the item is to be created
fields: The values of the columns set on this list item.
Returns
None
"""
url = f"https://graph.microsoft.com/v1.0/sites/{site_id}/lists/{list_id}/items/"
payload = {}
if fields:
payload["fields"] = eval(fields)
create_an_entity(url=url, payload=payload, bearer_token=self.bearer_token)The eval function appears to be used for parsing valid Python data types from arbitrary user input but has the side effect of enabling arbitrary code execution because Python code can be passed to it via the method explained above.
Pickle Load on BYOM model load leads to arbitrary code execution
CVE Number
CVE-2024-45852
Summary
A vulnerability exists within the decode function of the mindsdb/integrations/handlers/byom_handler/proc_wrapper.py file, which will perform a pickle.loads on a custom model built via the Build Your Own Model process. An attacker authenticated to a MindsDB instance can inject a malicious pickle object containing arbitrary code into the BYOM model build process using the ‘Upload Custom Model’ feature. This object will be deserialized when the model is loaded via a ‘predict’ or ‘describe’ query; executing the arbitrary code on the server.
Products Impacted
This vulnerability is present in MindsDB versions v23.3.2.0 or newer.
CVSS Score: 8.8
AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-502: Deserialization of Untrusted Data
Details
To exploit this vulnerability, an attacker authenticated to a MindsDB instance can create a Python script to train a model on a dataset and make predictions. Within this script, an attacker can include a class to create a malicious pickle object within the method used to train the model. A predict method and describe method can also be defined within the script. The attacker can then use the ‘Upload Custom Model’ feature within the MindsDB UI to upload the script, along with the related requirements.txt file, which would need to contain any libraries required to successfully achieve the exploit. They can then upload the relevant dataset as a file and use the appropriate SQL query to train the model with it.
When the model is trained, it is serialized along with the malicious pickle object due to the use of pickle.dumps within the encode function of the mindsdb/integrations/handlers/byom_handler/proc_wrapper.py file. When a prediction or describe query is run on the model, the relevant method (i.e., predict or describe) is called from within the ModelWrapperSafe class of the mindsdb/integrations/handlers/byom_handler/byom_handler.py file. This is the default behavior that ultimately leads to the calling of the vulnerable decode function of the mindsdb/integrations/handlers/byom_handler/proc_wrapper.py file, which performs pickle.loads to deserialize the model, as shown below:
def decode(encoded):
return pickle.loads(encoded)This function will deserialize the model along with the malicious pickle object, leading to any arbitrary code contained within it being executed on the server.
Pickle Load on inhouse BYOM model prediction leads to arbitrary code execution
CVE Number
CVE-2024-45853
Summary
A vulnerability exists within the predict method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file, which will perform pickle.loads on a custom model built via the Build Your Own Model process. An attacker authenticated to a MindsDB instance can inject a malicious pickle object containing arbitrary code into the BYOM model build process using the ‘Upload Custom Model’ feature. This object will be deserialized when the model is loaded via the ‘predict’ method; executing the arbitrary code on the server. Note this can only occur if the BYOM engine is changed in the config from the default ‘venv’ to ‘inhouse’.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.2.0 or newer.
CVSS Score: 7.1
AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
CWE Categorization
CWE-502: Deserialization of Untrusted Data
Details
To exploit this vulnerability, an attacker authenticated to a MindsDB instance can create a Python script to train a model on a dataset and make predictions. Within the script, an attacker can include a class to create a malicious pickle object within the method used to train the model. The attacker can use the ‘Upload Custom Model’ feature within the MindsDB UI to upload this Python script, along with the related requirements.txt file, which would need to contain any libraries required to successfully achieve the exploit. The attacker would then upload the relevant dataset as a file and use the appropriate SQL query to train the model with it and the uploaded script.
When the model is trained, it is serialized along with the malicious pickle object due to the use of pickle.dumps within the train method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file. The aforementioned class is used when the BYOM engine is changed to ‘inhouse’. When a prediction query is subsequently run on the model, the code is passed to the vulnerable predict method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file, which calls pickle.loads on the model, as shown below:
def predict(self, df, model_state, args):
model_state = pickle.loads(model_state)
self.model_instance.__dict__ = model_state
try:
result = self.model_instance.predict(df, args)
except Exception:
result = self.model_instance.predict(df)
return resultThis leads to the malicious pickle object being deserialized and any arbitrary code contained within it being executed on the server.
Pickle Load on inhouse BYOM model describe query leads to arbitrary code execution
CVE Number
CVE-2024-45854
Summary
A vulnerability exists within the describe method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file, which will perform pickle.loads on a custom model built via the Build Your Own Model process. An attacker authenticated to a MindsDB instance can inject a malicious pickle object containing arbitrary code into the BYOM model build process using the ‘Upload Custom Model’ feature. This object will be deserialized when the model is loaded via the ‘describe’ method; executing the arbitrary code on the server. Note this can only occur if the BYOM engine is changed in the config from the default ‘venv’ to ‘inhouse’.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.3.0 or newer.
CVSS Score: 7.1
AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
CWE Categorization
CWE-502: Deserialization of Untrusted Data
Details
To exploit this vulnerability, an attacker authenticated to a MindsDB instance can create a Python script to train a model on a dataset and make predictions. Within the script, an attacker can include a class to create a malicious pickle object within the method used to train the model. Also defined in the script will be a describe method, which can simply contain a pass statement. The attacker can use the ‘Upload Custom Model’ feature within the MindsDB UI to upload this Python script, along with the related requirements.txt file, which would need to contain any libraries required to successfully achieve the exploit. The attacker would then upload the relevant dataset as a file and use the appropriate SQL query to train the model with it and the uploaded script.
When the model is trained, it is serialized along with the malicious pickle object due to the use of pickle.dumps within the train method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file. The aforementioned class is used when the BYOM engine is changed to ‘inhouse’. When a describe query is subsequently run on the model (which can occur when a user clicks on the model in the UI to obtain information on it), the code is passed to the vulnerable describe method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file, which calls pickle.loads on the model, as shown below:
def describe(self, model_state, attribute: Optional[str] = None) -> pd.DataFrame:
if hasattr(self.model_instance, 'describe'):
model_state = pickle.loads(model_state)
self.model_instance.__dict__ = model_state
return self.model_instance.describe(attribute)
return pd.DataFrame()This leads to the malicious pickle object being deserialized and any arbitrary code contained within it being executed on the server.
Pickle Load on inhouse BYOM model finetune leads to arbitrary code execution
CVE Number
CVE-2024-45855
Summary
A vulnerability exists within the finetune method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file, which will perform pickle.loads on a custom model built via the Build Your Own Model process. An attacker authenticated to a MindsDB instance can inject a malicious pickle object containing arbitrary code into the BYOM model build process using the ‘Upload Custom Model’ feature. This object will be deserialized when the model is loaded via the ‘finetune’ method; executing the arbitrary code on the server. Note this can only occur if the BYOM engine is changed in the config from the default ‘venv’ to ‘inhouse’.
Products Impacted
This vulnerability is present in MindsDB versions v23.10.2.0 or newer.
CVSS Score: 7.1
AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H
CWE Categorization
CWE-502: Deserialization of Untrusted Data
Details
To exploit this vulnerability, an attacker authenticated to a MindsDB instance can create a Python script to train a model on a dataset and make predictions. Within the script, an attacker can include a class to create a malicious pickle object within the method used to train the model. The attacker can then use the ‘Upload Custom Model’ feature within the MindsDB UI to upload this Python script, along with the related requirements.txt file, which would need to contain any libraries required to successfully achieve the exploit. They can then upload the relevant dataset as a file and use the appropriate SQL query to train the model with it and the uploaded script.
When the model is trained, it is serialized along with the malicious pickle object due to the use of pickle.dumps within the train method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file. The aforementioned class is used when the BYOM engine is changed to ‘inhouse’. A finetune query can subsequently run on the model. Upon the query being run, the code is passed to the vulnerable finetune method of the ModelWrapperUnsafe class in the mindsdb/integrations/handlers/byom_handler/byom_handler.py file, which calls pickle.loads on the model, as shown below:
def finetune(self, df, model_state, args):
self.model_instance.__dict__ = pickle.loads(model_state)
call_args = [df]
if args:
call_args.append(args)
self.model_instance.finetune(df, args)
return pickle.dumps(self.model_instance.__dict__, protocol=5)This leads to the malicious pickle object being deserialized and any arbitrary code contained within it being executed on the server.
Web UI renders javascript code in ML Engine name leading to XSS
CVE Number
CVE-2024-45856
Summary
An attacker authenticated to a MindsDB instance can create an ML Engine, database, project, or upload a dataset within the UI and give it a name (or value in the dataset) containing malicious arbitrary javascript code. Whenever another user enumerates the items within the UI, the malicious arbitrary javascript code will run.
Products Impacted
The vulnerability is present in all versions of the MindsDB project.
CVSS Score: 9.0
AV:N/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H
CWE Categorization
CWE-79: Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’)
Details
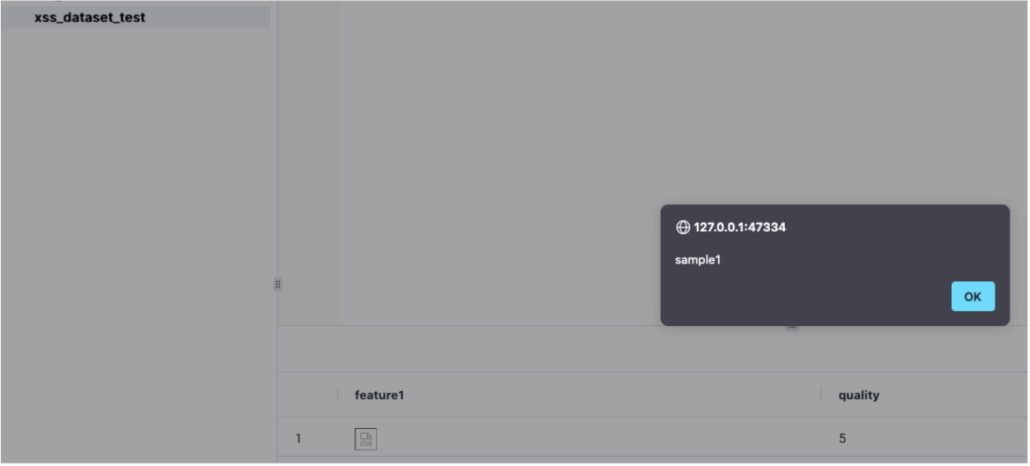
To exploit this vulnerability, an attacker authenticated to a MindsDB instance could craft a dataset as shown below:
feature1,quality
<img src='#' onerror=alert("sample1") />, 5Once this has been created, the attacker can upload the file, and the javascript code will be run in the victim’s browser when they attempt to view the contents of the dataset within the UI, as shown below:
As can be seen in the above screenshot, the rendering occurs within the table.
Timeline
July, 12 2024 — Vendor disclosure via process outlined in SECURITY.md
July, 23 2024 — Update made to project Github repository in version v24.7.4.1 replacing use of ‘eval’ with ‘ast.literal_eval’. This affects some of our submitted CVEs and can be seen here
July, 29 2024 — Follow up email sent to vendor
September, 6 2024 — Final attempt to reach out to vendor prior to public disclosure date
September, 10 2024 — Received response from vendor saying they had put a number of changes in place to “mitigate some or all of the reported issues”
September, 12 2024 — Public disclosure