HiddenLayer, a Gartner recognized Cool Vendor for AI Security, is the leading provider of Security for AI. Its security platform helps enterprises safeguard the machine learning models behind their most important products. HiddenLayer is the only company to offer turnkey security for AI that does not add unnecessary complexity to models and does not require access to raw data and algorithms. Founded by a team with deep roots in security and ML, HiddenLayer aims to protect enterprise’s AI from inference, bypass, extraction attacks, and model theft. The company is backed by a group of strategic investors, including M12, Microsoft’s Venture Fund, Moore Strategic Ventures, Booz Allen Ventures, IBM Ventures, and Capital One Ventures.
Jun 09, 2025
Exposure of sensitive Information allows account takeover
CVE Number
CVE-2025-49653
Summary
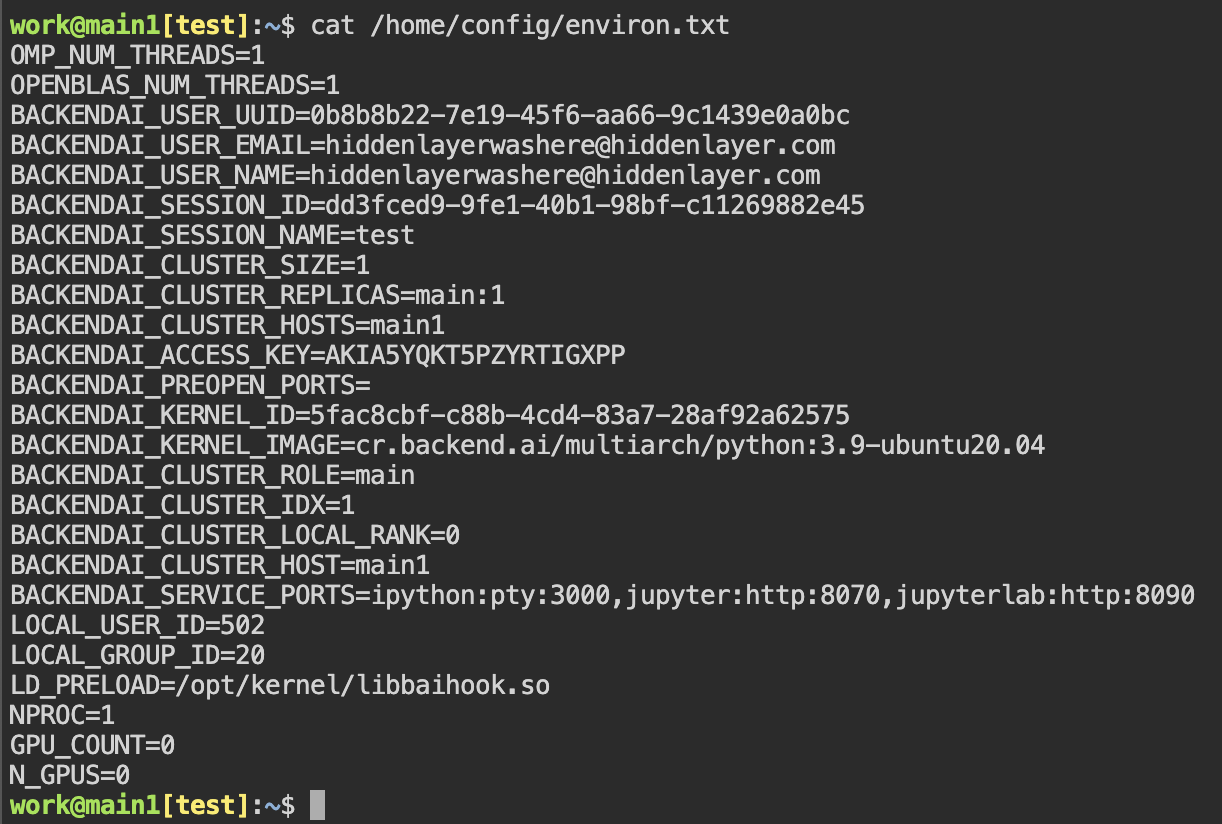
By default, BackendAI’s agent will write to /home/config/ when starting an interactive session. These files are readable by the default user. However, they contain sensitive information such as the user’s mail, access key, and session settings. A threat actor accessing that file can perform operations on behalf of the user, potentially granting the threat actor super administrator privileges.
Products Impacted
This vulnerability is present in all versions of BackendAI. We tested on version 25.3.3 (commit f7f8fe33ea0230090f1d0e5a936ef8edd8cf9959).
CVSS Score: 9.8
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-200: Exposure of Sensitive Information
Details
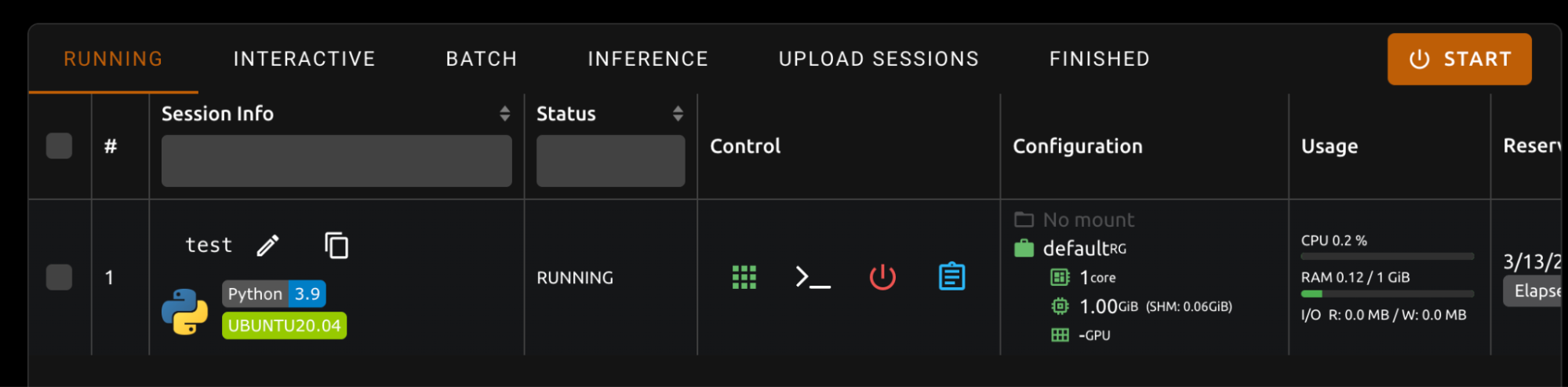
To reproduce this, we started an interactive session
Then, we can read /home/config/environ.txt and read the information.
Timeline
March 28, 2025 — Contacted vendor to let them know we have identified security vulnerabilities and ask how we should report them.
April 02, 2025 — Vendor answered letting us know their process, which we followed to send the report.
April 22, 2025 — Vendor responded, saying they don’t believe these are valid vulnerabilities.
April 22, 2025 — Follow up email sent, describing why these are valid vulnerabilities and saying we could get on a call with them to explain if necessary. We did not receive a response.