Missing Authorization for Interactive Sessions
June 9, 2025

Products Impacted
This vulnerability is present in all versions of BackendAI. We tested on version 25.3.3 (commit f7f8fe33ea0230090f1d0e5a936ef8edd8cf9959).
CVSS Score: 8.1
CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
CWE Categorization
CWE-862: Missing authorization
Details
When a user starts an interactive session, a web terminal gets exposed to a random port. A threat actor can scan the ports until they find an open interactive session and access it without any authorization or prior authentication.
To reproduce this, we created a session with all settings set to default.
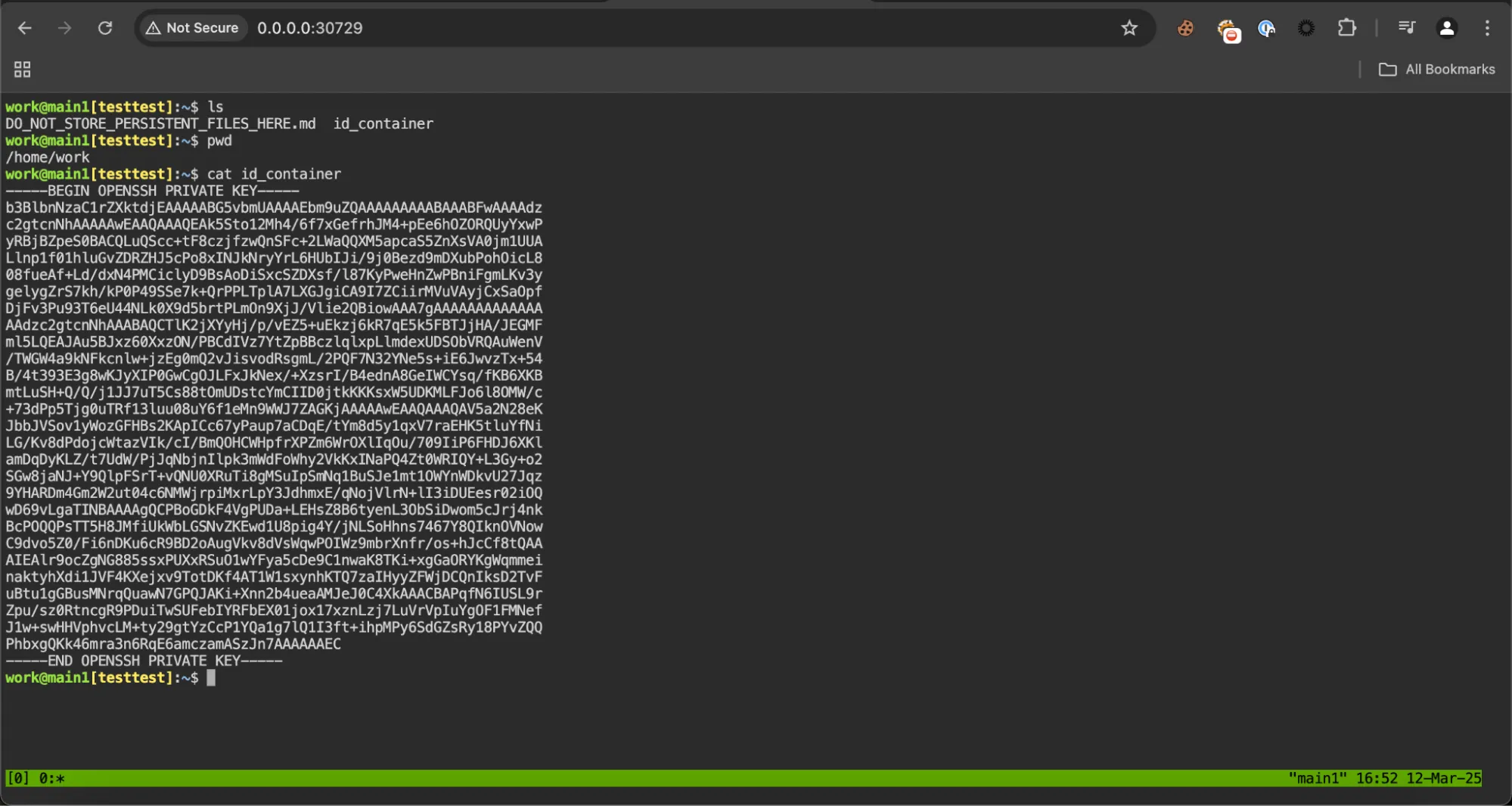
Then, we accessed the web terminal in a new tab
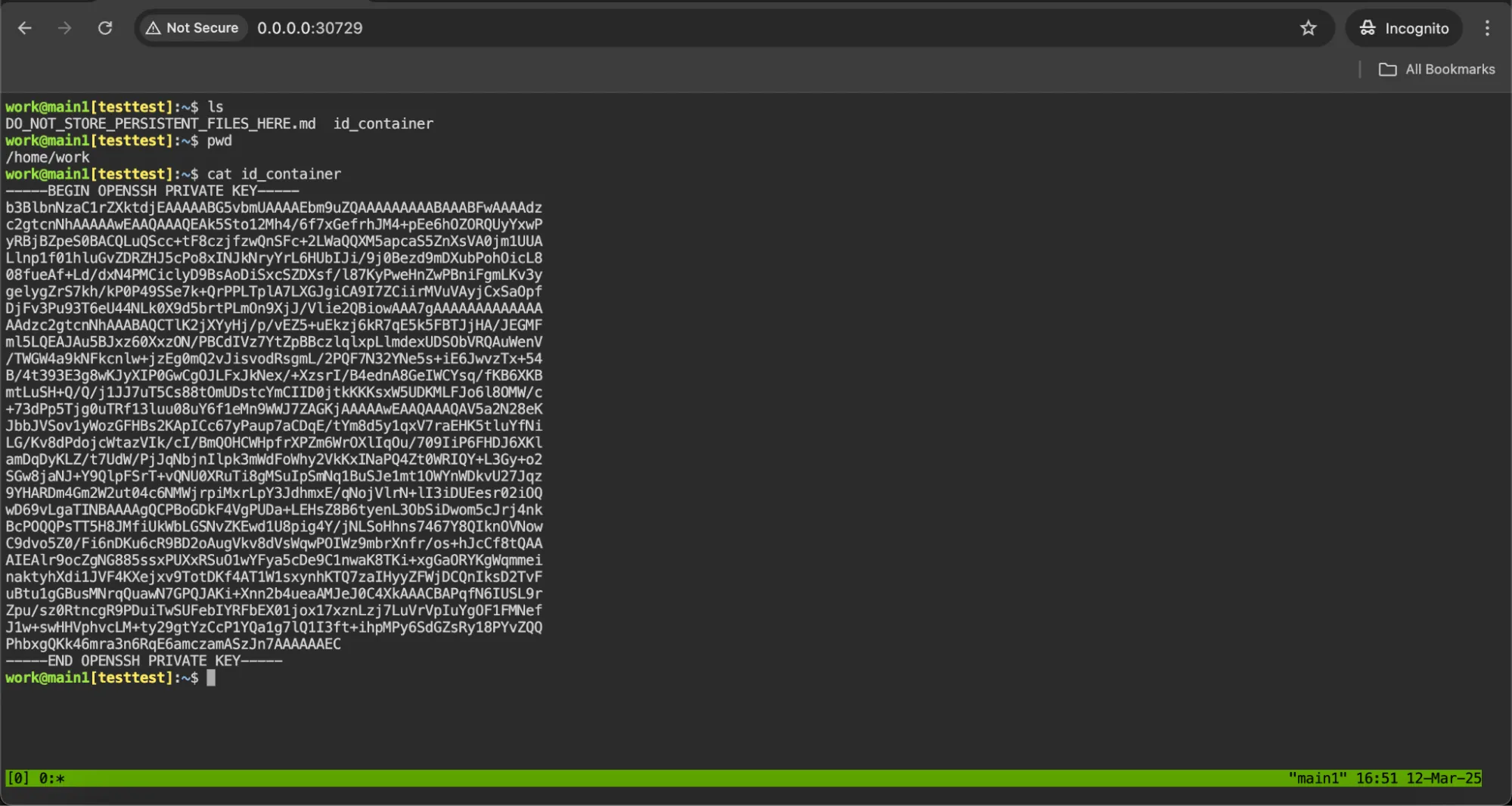
However, while simulating the threat actor, we access the same URL in an “incognito window” — eliminating any cache, cookies, or login credentials — we can still reach it, demonstrating the absence of proper authorization controls.
Related SAI Security Advisory
November 26, 2025
Allowlist Bypass in Run Terminal Tool Allows Arbitrary Code Execution During Autorun Mode
When in autorun mode, Cursor checks commands sent to run in the terminal to see if a command has been specifically allowed. The function that checks the command has a bypass to its logic allowing an attacker to craft a command that will execute non-allowed commands.
October 17, 2025
Path Traversal in File Tools Allowing Arbitrary Filesystem Access
A path traversal vulnerability exists within Windsurf’s codebase_search and write_to_file tools. These tools do not properly validate input paths, enabling access to files outside the intended project directory, which can provide attackers a way to read from and write to arbitrary locations on the target user’s filesystem.