Pickle Load in Read Pandas Utility Function
June 4, 2024

Products Impacted
This vulnerability is present in Ydata-profiling v3.7.0 or newer.
CVSS Score: 7.8
AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
CWE Categorization
CWE-502: Deserialization of Untrusted Data.
Details
In src/ydata_profiling/utils/dataframe.py pickle is used to load serialized pandas datasets within the read_pandas util function:
def read_pandas(file_name: Path) -> pd.DataFrame:
"""Read DataFrame based on the file extension. This function is used when the file is in a standard format.
Various file types are supported (.csv, .json, .jsonl, .data, .tsv, .xls, .xlsx, .xpt, .sas7bdat, .parquet)
Args:
file_name: the file to read
Returns:
DataFrame
Notes:
This function is based on pandas IO tools:
https://pandas.pydata.org/pandas-docs/stable/user_guide/io.html
https://pandas.pydata.org/pandas-docs/stable/reference/io.html
This function is not intended to be flexible or complete. The main use case is to be able to read files without
user input, which is currently used in the editor integration. For more advanced use cases, the user should load
the DataFrame in code.
"""
extension = uncompressed_extension(file_name)
if extension == ".json":
df = pd.read_json(str(file_name))
elif extension == ".jsonl":
df = pd.read_json(str(file_name), lines=True)
elif extension == ".dta":
df = pd.read_stata(str(file_name))
elif extension == ".tsv":
df = pd.read_csv(str(file_name), sep="\t")
elif extension in [".xls", ".xlsx"]:
df = pd.read_excel(str(file_name))
elif extension in [".hdf", ".h5"]:
df = pd.read_hdf(str(file_name))
elif extension in [".sas7bdat", ".xpt"]:
df = pd.read_sas(str(file_name))
elif extension == ".parquet":
df = pd.read_parquet(str(file_name))
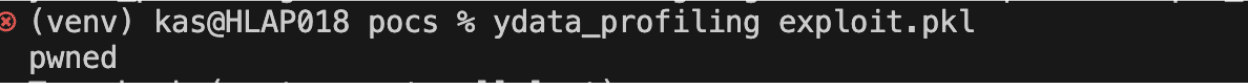
elif extension in [".pkl", ".pickle"]:
df = pd.read_pickle(str(file_name))While this function could be used by a user in code, the function is used by default when using the command line tool:
Related SAI Security Advisory
November 26, 2025
Allowlist Bypass in Run Terminal Tool Allows Arbitrary Code Execution During Autorun Mode
When in autorun mode with the secure ‘Follow Allowlist’ setting, Cursor checks commands sent to run in the terminal by the agent to see if a command has been specifically allowed. The function that checks the command has a bypass to its logic, allowing an attacker to craft a command that will execute non-whitelisted commands.
October 17, 2025
Data Exfiltration from Tool-Assisted Setup
Windsurf’s automated tools can execute instructions contained within project files without asking for user permission. This means an attacker can hide instructions within a project file to read and extract sensitive data from project files (such as a .env file) and insert it into web requests for the purposes of exfiltration.